
Account takeover fraud (ATO) has long plagued financial institutions. The digital banking revolution and eCommerce boom made ATO fraud an even greater menace.
The early 2000s witnessed the dawn of account takeover attacks. Stealthy fraudsters lured unsuspecting customers into phishing traps. They bet on their naivete in navigating the novel world of online banking and the bet paid off.
The modern-day ATO landscape is a battleground, with financial institutions grappling to counteract the onslaught of ATO fraud. As customers wised up and financial institutions fortified their defenses, cybercriminals evolved. They turned to the dark arts of social engineering and malware assaults. Meanwhile, annual losses skyrocket into the billions.
Fear not, for the guardians of finance have risen to the challenge, wielding an arsenal of cutting-edge security measures. Multi-factor authentication, behavioral biometrics, and machine learning-based fraud detection systems serve as the stalwart protectors of customer assets.
Let’s dig into what account takeover fraud is exactly, how it’s executed, and what can be done about it.
What is Account Takeover Fraud?
Account takeover fraud is a type of cybercrime where unauthorized individuals access and control someone else’s online accounts. Their typical intention is to steal funds or personal information. ATO fraud can affect businesses and individuals alike, leading to financial loss and reputational damage.
3 Types of Account Takeover Fraud
The three types of account takeover fraud are credential stuffing, phishing, and man-in-the-middle attacks. Let’s examine each of these more closely.
Credential Stuffing
Credential stuffing is a sinister cyberattack strategy that unleashes a barrage of previously stolen username-password combinations. The goal of credential stuffing is to gain unauthorized access to user accounts.
This sneaky technique thrives on the unfortunate human tendency to reuse login credentials across multiple platforms. Making the most of this weakness, fraudsters skillfully exploit the treasure trove of data breaches for their personal gain.
By taking over accounts on popular websites, criminals steal identities, commit financial fraud, or even hold your customers’ digital lives hostage. Educate customers about the dangers of ATO fraud.

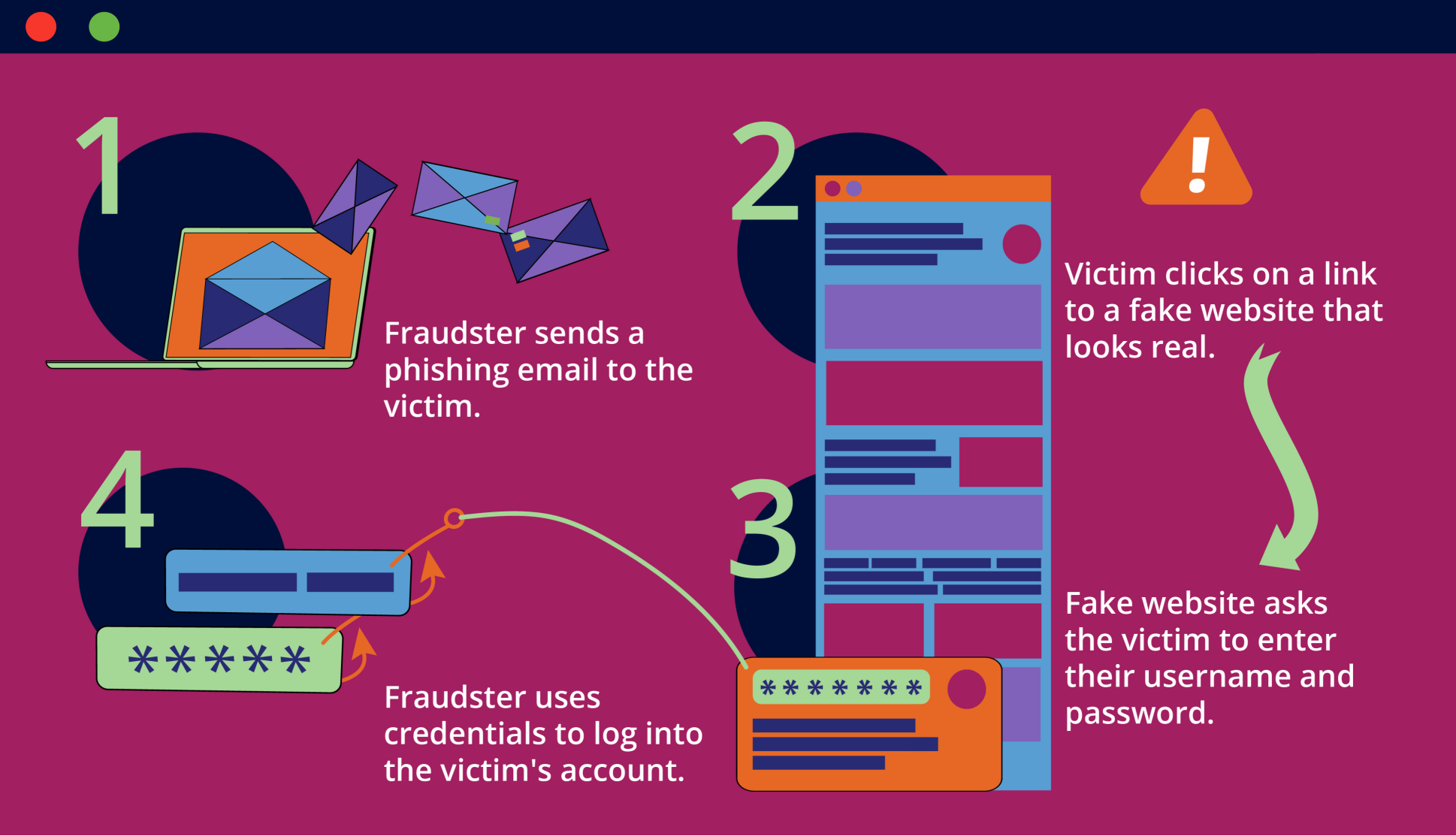
Phishing
Phishing is a cunning and deceptive technique fraudsters employ to bait unsuspecting individuals into revealing sensitive information, such as login credentials. Like master illusionists, cyber criminals craft authentic-looking emails, text messages, or even social media messages. With the aid of new techniques like generative AI, it’s easy for them to pass as legitimate businesses or trusted contacts.
The fraudster’s ultimate goal is to lure victims into clicking on harmful links or downloading infected attachments. Either of these actions could compromise someone’s digital life. These virtual con artists swindle vast sums of money or steal precious data by preying on human curiosity, trust, and urgency.
To help your customers avoid becoming the catch of the day, encourage them to remain vigilant. Everyone should double-check the source of any communication that seems fishy. Caution can help ensure we all swim safely in the vast ocean of the internet.
Man-in-the-Middle Attacks
Man-in-the-middle attacks are a devious form of digital eavesdropping. Fraudsters slyly intercept and manipulate the communication between two unsuspecting parties. These cybercriminals masquerade as trusted entities in the conversation, fooling their targets into believing they are engaging with legitimate counterparts.
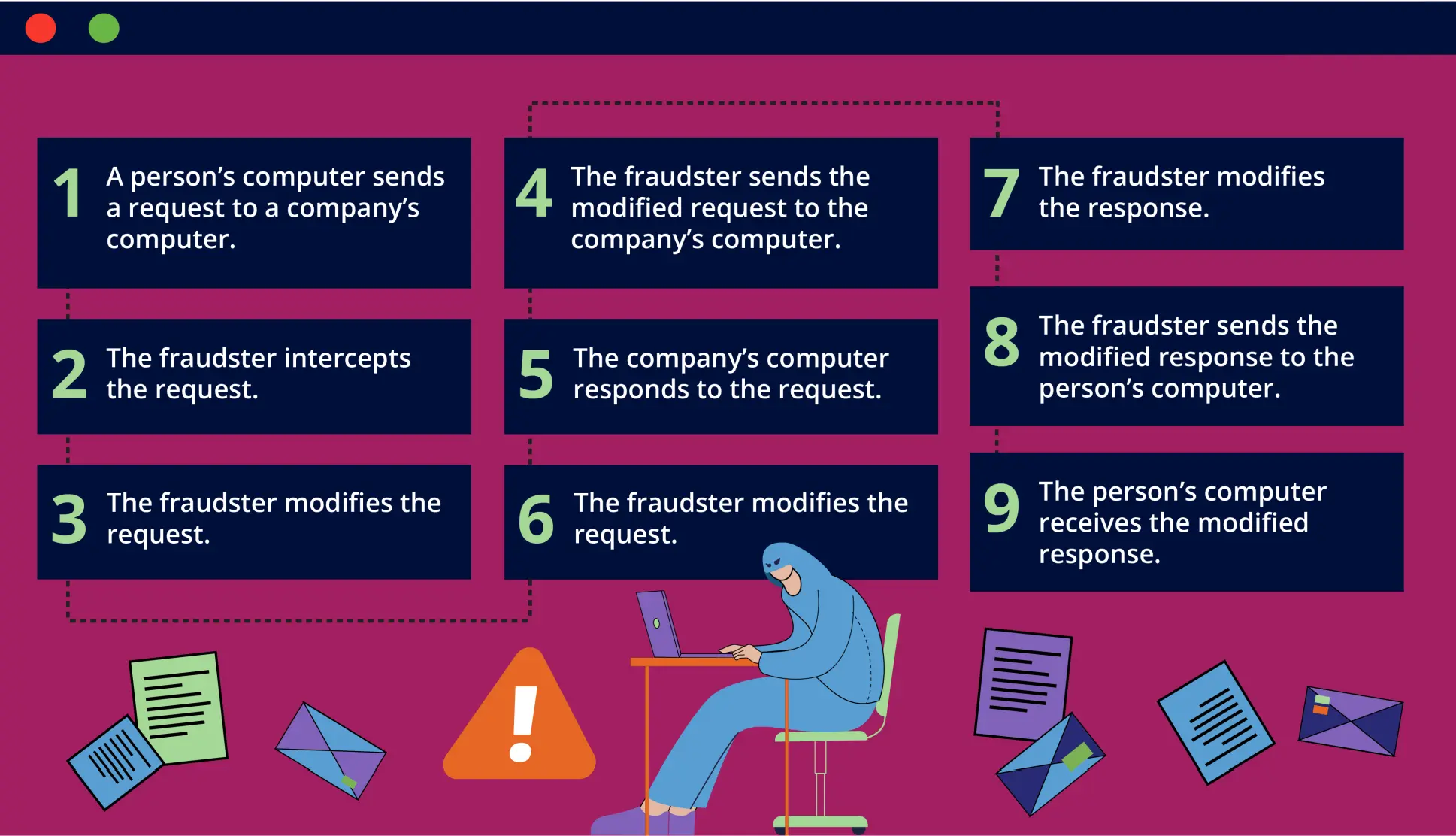
By controlling the flow of information, these digital puppet masters can steal sensitive data, inject malicious content, or even sabotage transactions. The lure of valuable insights, monetary gains, and the power to exploit vulnerabilities drives fraudsters to employ this treacherous technique.
3 Common Methods Used in ATO Fraud
Social engineering, malware, and brute force attacks are common methods for account takeover fraud. Let’s examine this sinister trifecta of ATO methods, each allowing fraudsters to control victims’ online accounts.
Social Engineering
Social engineering is a technique that exploits human psychology. It manipulates trust and emotions to trick users into divulging sensitive information or granting access to their accounts. Fraudsters thrive on this technique as it requires minimal technical prowess yet yields substantial rewards.
Malware
Conversely, malware infiltrates devices like a digital parasite, stealthily monitoring, stealing, or even corrupting data. Its effectiveness lies in its ability to cloak itself in seemingly innocuous files or programs, catching victims off guard.
Brute Force Attacks
Brute force attacks are powerful algorithms that tirelessly hammer away at login credentials until the fortress crumbles.
Understanding these account takeover fraud techniques is crucial for banks to protect their customers’ assets. It also maintains banks’ reputation as a secure financial institution.
Social engineering, malware, and brute force attacks are powerful weapons in the fraudster’s arsenal. Yet, they are just some of the most common ATO fraud techniques criminals use. Sadly, there are more, and no doubt, more are being developed every day.
ATO Fraud Leads to Financial Losses
The financial impact of ATO fraud can be nothing short of devastating for businesses and individuals alike. Direct monetary losses stemming from unauthorized transactions can be large, leaving victims reeling from the consequences.
For businesses, this translates to depleted revenue, strained customer relationships, and jeopardized future prospects. Individuals must face the harsh reality of drained savings, compromised credit scores, and the difficult task of rebuilding their financial history.
The ripple effect of ATO fraud extends far beyond the initial monetary losses. It casts a long shadow over the stability and well-being of those affected.

8 Account Takeover Fraud Prevention Techniques
Now that we’ve covered how ATO fraud is perpetrated and the devastation it creates, let’s fight back! Here are some of the most effective ATO fraud prevention techniques.
Multi-factor authentication
One of the most widely used ATO fraud prevention techniques is multi-factor authentication (MFA). MFA adds extra security to the login process, requiring users to provide multiple forms of identification to gain access. This could include something they know, such as a password, something they have, such as a security token or phone, or something they are, such as biometric data.
Risk-based authentication (RBA)
Another effective ATO fraud prevention technique is risk-based authentication (RBA). RBA evaluates the risk of a login attempt based on factors such as location, device, and behavior. If a login attempt is deemed high-risk, the system can require additional authentication steps or deny access altogether.
Real-time monitoring
Real-time monitoring is also a critical component of ATO fraud prevention. By continuously monitoring user activity, businesses can quickly detect any suspicious behavior and take action to prevent fraudulent activity. Behavioral analytics and machine learning are powerful tools that can help identify anomalous behavior patterns and detect potential ATO fraud attempts.
Biometric authentication
Biometric data, such as an eye scan, facial recognition, or fingerprints, is unique for each person and impossible to duplicate. By using biometric authentication, banks can accurately verify their customer’s identity. This makes it much more difficult for fraudsters to take over accounts.
Anomaly detection with behavioral biometrics
Anomaly detection with behavioral biometrics is one of the most powerful techniques for detecting ATO fraud. Behavioral biometrics analyze user behavior patterns, such as typing speed, mouse movements, and other unique behavioral characteristics. By analyzing these patterns, banks can detect any anomalies that might indicate fraudulent activity, such as unusual login times or devices.
Device fingerprinting
Device fingerprinting tracks unique characteristics of the device being used, such as the IP address, screen size, and browser type. By tracking device fingerprint data, banks can detect when a user logs in from an unfamiliar device or location. Either of these scenarios can indicate a fraudulent login attempt.
IP geolocation
IP geolocation technology uses a device’s IP address to determine its geographic location. By monitoring IP addresses and their associated locations, banks can detect when a user is logging in from a suspicious location, such as a different country or region.
Machine learning
Machine learning is another powerful tool for detecting ATO fraud. By analyzing vast amounts of data, machine learning algorithms can detect subtle patterns and anomalies that might indicate fraudulent activity. Machine learning can also help identify new and emerging fraud trends, allowing banks to stay ahead of fraudsters.
AI is at the heart of advanced ATO fraud detection technology, and its role cannot be overstated. Using advanced AI algorithms allows banks to analyze massive amounts of data in real time. They can detect suspicious behavior patterns and respond quickly to prevent fraud. AI also identifies new and emerging fraud trends so banks stay ahead of the curve and protect their customers from harm.
Best Practices for Detecting ATO Fraud
In addition to these techniques, there are several best practices that banks can follow to minimize their risk of ATO fraud. These include:
- Monitoring user activity for signs of suspicious behavior on a regular basis
- Limiting the number of login attempts a user can make in a given session
- Educating users about password security and the importance of keeping their personal information secure.
Unleashing Machine Learning’s Power to Prevent Account Takeover Fraud
Machine learning is a game-changer in combating account takeover fraud. Let’s look at just some of the ways AI empowers fraud detection and prevention:
🎯 Fraud Scoring: Machine learning algorithms can analyze large datasets of customer behavior to identify patterns of fraudulent activity. By ranking each login or transaction by risk, they help fraud managers zero in on events that warrant further scrutiny.
🚩 Anomaly Detection: Train machine learning algorithms to spot oddities in customer accounts. If a customer suddenly logs in using a new device or location, algorithms raise a red flag. This prompts fraud managers to investigate.
🔮 Predictive Analytics: Harness machine learning to predict customers who are vulnerable to account takeover fraud. By analyzing customer behavior patterns, machine learning algorithms identify risky individuals and suggest proactive measures to prevent fraud.
🔄 Continuous Learning: Machine learning algorithms evolve. This allows them to adapt to new fraud patterns and boost their account takeover fraud detection and prevention prowess over time. By constantly updating their models with new data, they stay ahead of fraudsters’ tactics.
In a nutshell, machine learning elevates banks’ ability to swiftly and accurately detect and prevent account takeover fraud. By automating fraud detection and analysis, algorithms liberate fraud managers to concentrate on high-risk cases and proactive fraud prevention.
8 Must-Have Features of a Cutting-Edge Account Takeover Fraud Solution for Banks
Banks interested in a machine learning solution to detect and prevent ATO fraud should look for the following key features:
🕒 Real-time monitoring: Choose an ATO solution that provides real-time transaction monitoring of all customer transactions and account activity. Real-time monitoring allows banks to quickly detect any suspicious behavior.
🔑 Multi-factor authentication: Look for strong authentication measures, such as multi-factor authentication, securing account access only for authorized users.
📊 Behavioral analytics: The account takeover fraud solution should use behavioral analytics to track patterns of user behavior. Tracking user behavior patterns allows banks to learn their users’ genuine habits and detect anomalies that could indicate fraud.
🤖 Machine learning and AI: Opt for a solution with machine learning and AI at its core. Machine learning constantly adapts to the fraud landscape and enhances fraud detection.
⚖️ Risk scoring: The account takeover fraud solution should provide risk scores for each transaction or account activity. The risk score is based on the likelihood of fraud.
🧩 Seamless integration: Find a flexible solution that plays well with your bank’s existing systems and is easy to integrate and customize.
📈 Comprehensive reporting: Choose a solution with comprehensive reporting capabilities, empowering your bank to monitor and analyze fraud trends and patterns.
📃 Compliance: The account takeover fraud solution should comply with all relevant regulations and standards. An example of this is the Payment Card Industry Data Security Standard (PCI DSS) or the General Data Protection Regulation (GDPR).
In a nutshell, machine learning elevates banks’ ability to swiftly and accurately detect and prevent account takeover fraud. By automating fraud detection and analysis, algorithms liberate fraud managers to concentrate on high-risk cases and proactive fraud prevention.
Resources for Account Takeover Fraud Prevention
We hope our exploration of account takeover fraud prevention and detection has armed you with the knowledge to outsmart nefarious cybercriminals.
Here are additional resources for account takeover fraud prevention:
- Article: How to Boost Fraud Detection to Combat ATO Fraud
- Resource: Account Takeover Fraud: Becoming Preventative vs. Reactionary
- Solution Guide: Prevent Account Takeover Attacks
- Solution: Feedzai’s Digital Trust
Share this article:
Related Posts
0 Comments4 Minutes
Feedzai’s AI Technology Earns Industry Recognition by Chartis
Feedzai, the world’s first RiskOps platform, has secured a pair of critical recognitions…
0 Comments6 Minutes
10 Fraud Prevention Tips for Businesses
Hopefully, you’ve had a chance to read Feedzai’s James Hunt’s insightful conversation…
0 Comments7 Minutes
Beyond the Face: Why Vietnam’s Banks Need Behavioral Biometrics to Fight the Rising Tide of Fraud
Financial transactions are increasingly virtual in today’s digital age, making fraud…
